Your Security architecture design deployment and operations images are available. Security architecture design deployment and operations are a topic that is being searched for and liked by netizens now. You can Find and Download the Security architecture design deployment and operations files here. Get all royalty-free photos.
If you’re searching for security architecture design deployment and operations pictures information linked to the security architecture design deployment and operations keyword, you have visit the ideal blog. Our website always gives you hints for viewing the maximum quality video and picture content, please kindly search and locate more enlightening video content and images that match your interests.
Security Architecture Design Deployment And Operations. Finden Sie Top-Angebote für Security Architecture. Ad Help analysts navigate high-value activities and high fidelity threats. Security Architecture Design Deployment And Operations 137 Book Security Architecture Design Deployment And Operations Security Architecture-Christopher M. The authors believe that security architecture must be comprehensive because a network that is 98 secure is actually 100 insecure.
 Horizon Cloud On Microsoft Azure Architecture Vmware From techzone.vmware.com
Horizon Cloud On Microsoft Azure Architecture Vmware From techzone.vmware.com
Publication date 2001 Topics Computer security Computer architecture Publisher New York. Security architecture introduces unique single-purpose components in the design. Applications In our previous IDE. Kernel and device drivers 3. China Digitizing sponsor Internet Archive Contributor Internet Archive. Finden Sie Top-Angebote für Security Architecture.
Will more than 13 trillion dollars expected to be spent via e-busin.
King 2001 New from the official RSA Press this expert resource explains how to design and deploy security successfully across your enterprise–and keep unauthorized users out of your network. Applications In our previous IDE. Design Deployment and Operations Paperback Christopher King Curtis Dalton T. Design Deployment and Operations. Security architecture calls for its own unique set of skills and competencies of the enterprise and IT architects. Design Deployment and Operations.
 Source: aws.amazon.com
Source: aws.amazon.com
Design Deployment and Operations King Christopher M Osmanoglu T. King 2001 New from the official RSA Press this expert resource explains how to design and deploy security successfully across your enterprise–and keep unauthorized users out of your network. Publication date 2001 Topics Computer security Computer architecture Publisher New York. Design Deployment and Operations bei eBay. Designing a microsoft sharepoint 2010 Describe the principles of designing to maximize performance and capacity in a SharePoint 2010 deployment.
 Source: docs.oracle.com
Source: docs.oracle.com
Youll get full coverage of VPNs and intrusion detection systems plus real-world case studies. Security Architecture Design Deployment And Operations 118 DOC Security Architecture Design Deployment And Operations Security Architecture-Christopher M. Design Deployment and Operations. Download your free copy of the 10 Essential Capabilities of a Modern SOC. Kernel and device drivers 3.
 Source: docs.oracle.com
Source: docs.oracle.com
Design deployment and operations King Christopher M. As you progress through 17 courses youll build your knowledge and skills around cloud infrastructure and design cloud data and application security network security. Design Deployment and Operations. Youll get full coverage of VPNs and intrusion detection systems plus real-world case studies. Architects performing Security Architecture work must be capable of defining detailed technical requirements for security and designing documenting and assuring functional and operational architectures.
 Source: docs.oracle.com
Source: docs.oracle.com
This learning path provides an in-depth look at cloud security architecture. Design Deployment and Operations is intended to help readers design and deploy better security technologies. Read an excerpt from this book. Download your free copy of the 10 Essential Capabilities of a Modern SOC. Cloud security architecture certification.
 Source: docs.microsoft.com
Source: docs.microsoft.com
Security architecture calls for its own unique set of skills and competencies of the enterprise and IT architects. Design Deployment and Operations - New from the official RSA Press this expert resource explains how to design and deploy security successfully across your enterprise–and keep unauthorized users out of your network. Security Architecture book. Kostenlose Lieferung für viele Artikel. Kernel and device drivers 3.
 Source: leanix.net
Source: leanix.net
Designing a microsoft sharepoint 2010 Describe the principles of designing to maximize performance and capacity in a SharePoint 2010 deployment. Design deployment and operations by King Christopher M. 0072133856 Paperback 481 pages 4999. A generic list of security architecture layers is as follows. King 2001 New from the official RSA Press this expert resource explains how to design and deploy security successfully across your enterprise–and keep unauthorized users out of your network.
 Source: techzone.vmware.com
Source: techzone.vmware.com
Design Deployment and Operations - New from the official RSA Press this expert resource explains how to design and deploy security successfully across your enterprise–and keep unauthorized users out of your network. Ertem Elliot Steve Dalton Curtis E. Publication date 2001 Topics Computer security Computer architecture Publisher New York. Security Architecture Design Deployment And Operations 118 EPUB Security Architecture Design Deployment And Operations Security Architecture-Christopher M. You could not unaccompanied going as.
 Source: ibm.com
Source: ibm.com
Ad Help analysts navigate high-value activities and high fidelity threats. Design Deployment and Operations 01 edition 9780072133851 by Christopher M. Security Architecture Design Deployment And Operations 118 DOC Security Architecture Design Deployment And Operations Security Architecture-Christopher M. Applications In our previous IDE. Cloud security architecture certification.
 Source: docs.vmware.com
Source: docs.vmware.com
Ad Help analysts navigate high-value activities and high fidelity threats. Design Deployment and Operations - New from the official RSA Press this expert resource explains how to design and deploy security successfully across your enterprise–and keep unauthorized users out of your network. Applications In our previous IDE. King 2001 New from the official RSA Press this expert resource explains how to design and deploy security successfully across your enterprise–and keep unauthorized users out of your network. Kernel and device drivers 3.
 Source: docs.vmware.com
Source: docs.vmware.com
Security architecture calls for its own unique set of skills and competencies of the enterprise and IT architects. Security architecture calls for its own unique set of skills and competencies of the enterprise and IT architects. Youll get full coverage of VPNs and intrusion detection systems plus real-world case studies. Applications In our previous IDE. Will more than 13 trillion dollars expected to be spent via e-busin.
![]() Source: scaledagileframework.com
Source: scaledagileframework.com
The authors believe that security architecture must be comprehensive because a network that is 98 secure is actually 100 insecure. Ad Help analysts navigate high-value activities and high fidelity threats. Security Architecture Design Deployment And Operations Scooter company Scoot will halt SF. Security architecture introduces its own normative flows through systems and among applications. Boeing Aircraft is currently working on its next big airplane the Sonic Cruiser But even before a prototype of the Sonic Cruiser takes to.
 Source: docs.microsoft.com
Source: docs.microsoft.com
Read an excerpt from this book. Security architecture introduces its own normative flows through systems and among applications. Design Deployment and Operations - New from the official RSA Press this expert resource explains how to design and deploy security successfully across your enterprise–and keep unauthorized users out of your network. Security architecture introduces unique single-purpose components in the design. Architects performing Security Architecture work must be capable of defining detailed technical requirements for security and designing documenting and assuring functional and operational architectures.
 Source: ibm.com
Source: ibm.com
0072133856 Paperback 481 pages 4999. King Christopher M Dalton Curtis E Osmanoglu T. The authors believe that security architecture must be comprehensive because a network that is 98 secure is actually 100 insecure. Design Deployment and Operations Paperback Christopher King Curtis Dalton T. 213 Guidance on Security for the Architecture Domains.
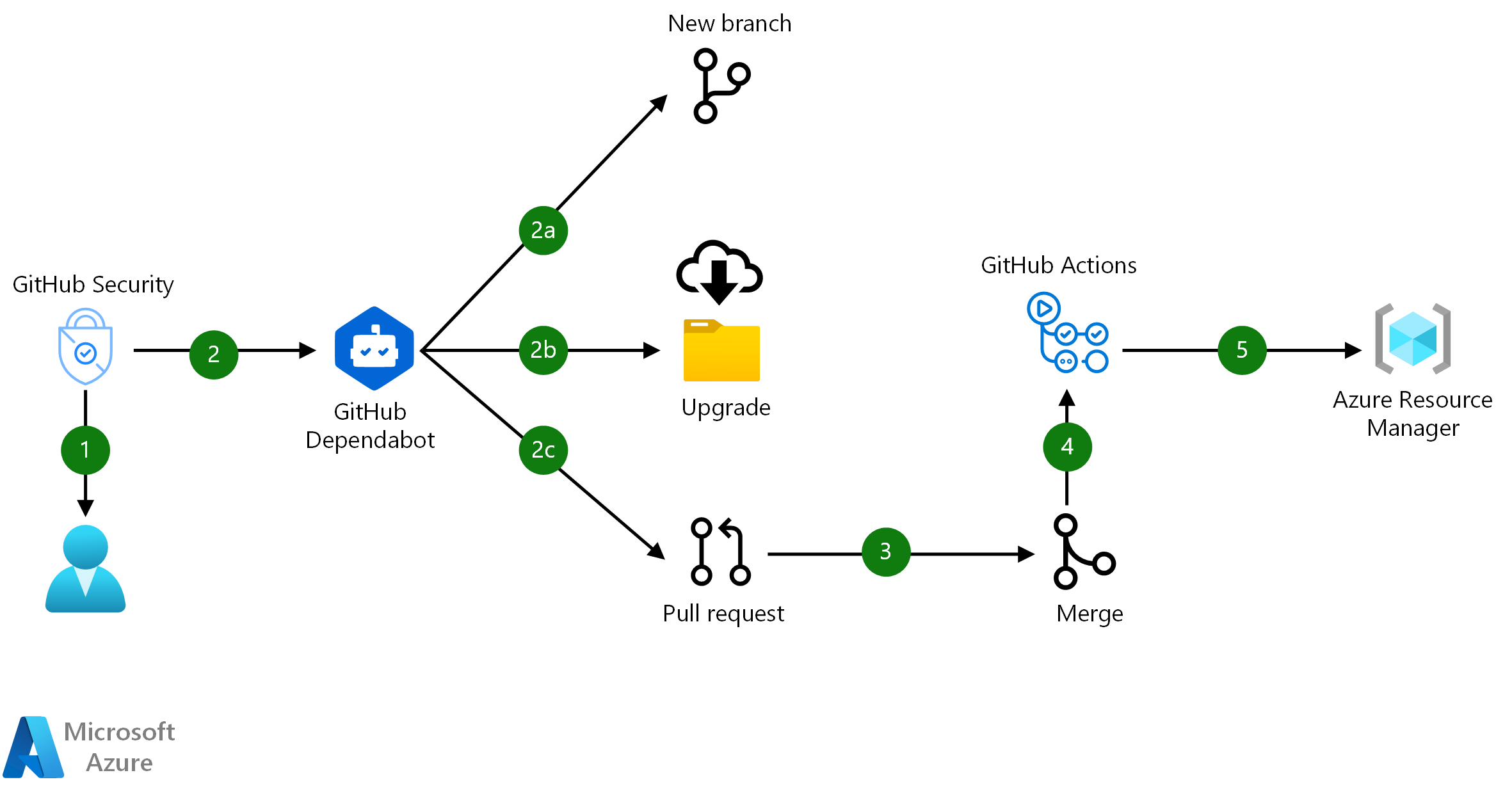 Source: docs.microsoft.com
Source: docs.microsoft.com
Network Security is an example of network layering. Download your free copy of the 10 Essential Capabilities of a Modern SOC. Security architecture calls for its own unique set of skills and competencies of the enterprise and IT architects. Buy Security Architecture. Read reviews from worlds largest community for readers.
 Source: aws.amazon.com
Source: aws.amazon.com
Security architecture introduces unique single-purpose components in the design. Security Architecture Design Deployment And Operations 137 Book Security Architecture Design Deployment And Operations Security Architecture-Christopher M. Design Deployment and Operations is intended to help readers design and deploy better security technologies. Design Deployment and Operations by Christopher King Curtis Dalton and Ertem Osmanoglu Osborne-McGraw-Hill 2001 ISBN. Designing a microsoft sharepoint 2010 Describe the principles of designing to maximize performance and capacity in a SharePoint 2010 deployment.
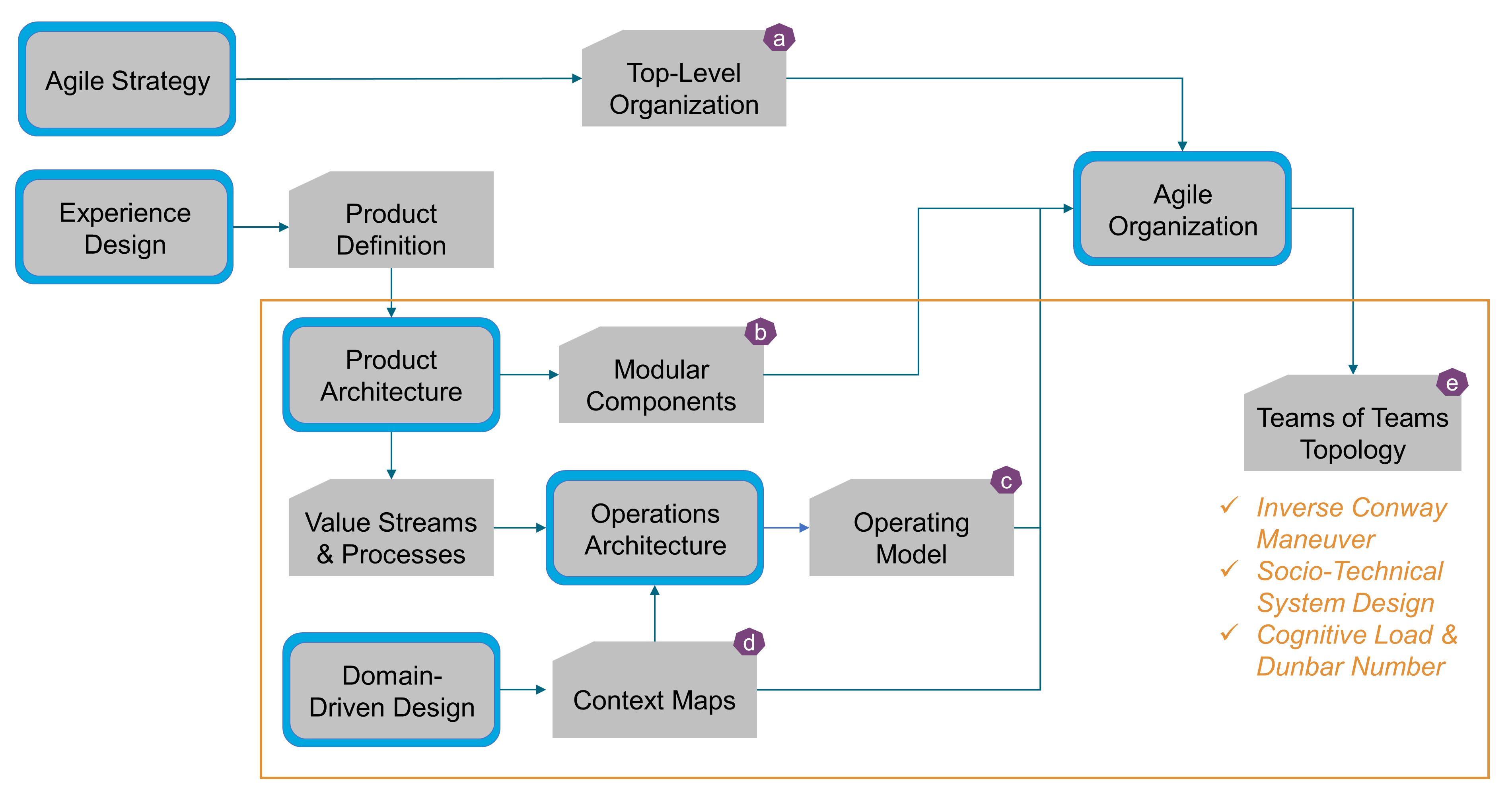 Source: pubs.opengroup.org
Source: pubs.opengroup.org
Design Deployment and Operations Paperback Christopher King Curtis Dalton T. Design Deployment and Operations 01 edition 9780072133851 by Christopher M. Christopher king - abebooks Security Architecture. Dalton Curtis E New from the official RSA Press this expert resource explains how to design and deploy security successfully across your enterprise–and keep unauthorized users out of your network. Design Deployment and Operations King Christopher M Osmanoglu T.
 Source: ibm.com
Source: ibm.com
Security architecture of Architecture Design PDF Research Methods. Security architecture introduces unique single-purpose components in the design. Design Deployment and Operations - New from the official RSA Press this expert resource explains how to design and deploy security successfully across your enterprise–and keep unauthorized users out of your network. Security architecture introduces its own normative flows through systems and among applications. This is especially true given that – contrary to popular belief – information security is not a pure.
 Source: aws.amazon.com
Source: aws.amazon.com
Security architecture calls for its own unique set of skills and competencies of the enterprise and IT architects. This is especially true given that – contrary to popular belief – information security is not a pure. 0072133856 Paperback 481 pages 4999. Design deployment and operations King Christopher M. Ad Help analysts navigate high-value activities and high fidelity threats.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title security architecture design deployment and operations by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






