Your Cyber security architecture design images are available in this site. Cyber security architecture design are a topic that is being searched for and liked by netizens now. You can Download the Cyber security architecture design files here. Get all royalty-free vectors.
If you’re looking for cyber security architecture design images information related to the cyber security architecture design interest, you have visit the right site. Our site frequently gives you hints for downloading the maximum quality video and picture content, please kindly hunt and find more enlightening video content and graphics that fit your interests.
Cyber Security Architecture Design. At this phase the design and architecture of security services are. What Is Security Architecture and Design. The collective features of a cybersecurity architecture include but are not limited to. Furthermore a properly implemented security architecture must achieve certain key objectives including.
 Pin On Cybersecurity From pinterest.com
Pin On Cybersecurity From pinterest.com
The first part covers the hardware and software required to have a secure computer system. Prepare technical reports that document the system development process. Our service includes consultancy support guidance and advice on the following areas. Provide structure coherence and cohesiveness. Security Architecture and Design is a three-part domain. Who is a Cyber Security Architect.
Legislative and legal requirements.
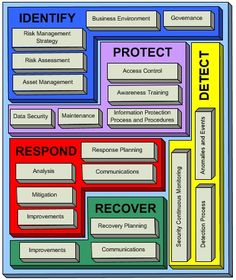
Security Architecture and Design is a three-part domain. Cyber security architecture maintains the systems quality attributes such as confidentiality integrity and availability. Cyber Security Architecture Our team of cyber security experts can help in developing designing and implementing secure architectures across IT systems networks and applications. A cybersecurity architect sometimes just called a security architect is responsible for designing creating and maintaining the security systems within an organizations IT network including the computer systems and data. Who is a Cyber Security Architect. This initial post focuses on the importance of identifying an organizations critical assets and data so it can design a cybersecurity architecture that incorporates controls to protect those systems.
 Source: pinterest.com
Source: pinterest.com
Security architecture translates the business requirements to executable security requirements. Security Architecture and Design. Conduct security reviews and identify gaps in security architectures and designs eg firewall virtual private networks routers servers etc. Cyber security architecture network security architecture or cyber architecture for short specifies the organizational structure functional behavior standards and policies of a computer network that includes both network and security features. The ideal candidate will have a strong Cyber Security Architecture background will be able to perform as a client-facing role and will be willing and.
 Source: pinterest.com
Source: pinterest.com
Security Architecture Security Architecture involves the design of inter- and intra- enterprise security solutions to meet client business requirements in application and infrastructure areas. The CyberML Cyber Modeling Language is a UML profile and model library for specifying the architectures and designs of cybersecurity applications. Cyber security architecture is the design artifacts that describe how the security controls are positioned and how they relate to the overall systems architecture. Design refers to how the security architecture is built. Since CyberML is designed and implemented as a UML profile UML dialect and model library it is compatible with the UML and OMG SysML architecture modeling language standards and can be implemented in popular.
 Source: pinterest.com
Source: pinterest.com
The ideal candidate will have a strong Cyber Security Architecture background will be able to perform as a client-facing role and will be willing and. What Is Cyber Resilience. Design refers to how the security architecture is built. Cyber security architecture is the design artifacts that describe how the security controls are positioned and how they relate to the overall systems architecture. Security architecture and design looks at how security controls are implemented to protect the confidentiality integrity and availability of systems around people processes and technology.
 Source: pl.pinterest.com
Source: pl.pinterest.com
Explore our collection of articles presentations. What Is Security Architecture and Design. Best Practices für mehr Cyber Security im Unternehmen. Legislative and legal requirements. Our Security Architecture Design and Implementation Services give you the expert insight you need to develop and implement security defenses to protect your corporate assets and client data.
 Source: pinterest.com
Source: pinterest.com
Best Practices für mehr Cyber Security im Unternehmen. The collective features of a cybersecurity architecture include but are not limited to. Security architecture and design looks at how information security controls and safeguards are implemented in IT systems in order to protect the confidentiality integrity and availability of the data that are used processed and stored in those systems. Security architecture translates the business requirements to executable security requirements. Security Architecture and Design.
 Source: pinterest.com
Source: pinterest.com
Who is a Cyber Security Architect. Cyber security architecture is the design artifacts that describe how the security controls are positioned and how they relate to the overall systems architecture. Here you evaluate the influence of vital business assets the risks and the effects of. Business and technology roadmaps. Ad Cyber Security Policy.
 Source: pinterest.com
Source: pinterest.com
While security architecture has many definitions ultimately it is a set of security principles methods and models designed to align to your objectives and help keep your organization safe from cyber threats. Security architecture and design looks at how security controls are implemented to protect the confidentiality integrity and availability of systems around people processes and technology. While security architecture has many definitions ultimately it is a set of security principles methods and models designed to align to your objectives and help keep your organization safe from cyber threats. Furthermore a properly implemented security architecture must achieve certain key objectives including. This post will be the first in a series focusing on common weaknesses in organizational cybersecurity architecture.
 Source: pinterest.com
Source: pinterest.com
Our service includes consultancy support guidance and advice on the following areas. Provide structure coherence and cohesiveness. Best Practices für mehr Cyber Security im Unternehmen. Furthermore a properly implemented security architecture must achieve certain key objectives including. Security architecture translates the business requirements to executable security requirements.
 Source: pinterest.com
Source: pinterest.com
Cyber security architecture is the design artifacts that describe how the security controls are positioned and how they relate to the overall systems architecture. What is security architecture. This initial post focuses on the importance of identifying an organizations critical assets and data so it can design a cybersecurity architecture that incorporates controls to protect those systems. As mentioned above security architecture refers to the systems processes and tools in place used to prevent or mitigate attacks. Wie können effektive Simulationen zu mehr Cyber Security führen.
 Source: pinterest.com
Source: pinterest.com
Conduct security reviews and identify gaps in security architectures and designs eg firewall virtual private networks routers servers etc. Who is a Cyber Security Architect. A basic definition of security architecture and design is that its a systematic approach to improving network security and mitigating risks. Security architecture and design looks at how security controls are implemented to protect the confidentiality integrity and availability of systems around people processes and technology. What Is Cyber Resilience.
 Source: pinterest.com
Source: pinterest.com
Ensure acquired or developed systems are consistent with cyber security policies and practices. The second part covers the logical models required to keep the system secure and the third part covers evaluation models that quantify how secure the system really is. Cyber Security Architecture Our team of cyber security experts can help in developing designing and implementing secure architectures across IT systems networks and applications. Prepare technical reports that document the system development process. Cybersecurityarchitectureanddesign CybersecurityThis is the first video of the three videos series on the topic - Cyber security architecture and design.
 Source: pinterest.com
Source: pinterest.com
As mentioned above security architecture refers to the systems processes and tools in place used to prevent or mitigate attacks. Ensure acquired or developed systems are consistent with cyber security policies and practices. Ad Cyber Security Policy. The second part covers the logical models required to keep the system secure and the third part covers evaluation models that quantify how secure the system really is. A well designed security architecture takes into consideration several change drivers including.
 Source: pinterest.com
Source: pinterest.com
Security architecture and design looks at how information security controls and safeguards are implemented in IT systems in order to protect the confidentiality integrity and availability of the data that are used processed and stored in those systems. As mentioned above security architecture refers to the systems processes and tools in place used to prevent or mitigate attacks. Security architecture and design looks at how information security controls and safeguards are implemented in IT systems in order to protect the confidentiality integrity and availability of the data that are used processed and stored in those systems. Who is a Cyber Security Architect. A cybersecurity architect sometimes just called a security architect is responsible for designing creating and maintaining the security systems within an organizations IT network including the computer systems and data.
 Source: pinterest.com
Source: pinterest.com
Cyber security architecture maintains the systems quality attributes such as confidentiality integrity and availability. This initial post focuses on the importance of identifying an organizations critical assets and data so it can design a cybersecurity architecture that incorporates controls to protect those systems. Security Architecture Security Architecture involves the design of inter- and intra- enterprise security solutions to meet client business requirements in application and infrastructure areas. Business and technology roadmaps. Security Architecture and Design.
 Source: pinterest.com
Source: pinterest.com
Our service includes consultancy support guidance and advice on the following areas. Cybersecurityarchitectureanddesign CybersecurityThis is the first video of the three videos series on the topic - Cyber security architecture and design. The CyberML Cyber Modeling Language is a UML profile and model library for specifying the architectures and designs of cybersecurity applications. Design refers to how the security architecture is built. A cybersecurity architect sometimes just called a security architect is responsible for designing creating and maintaining the security systems within an organizations IT network including the computer systems and data.
 Source: pinterest.com
Source: pinterest.com
Our Security Architecture Design and Implementation Services give you the expert insight you need to develop and implement security defenses to protect your corporate assets and client data. A basic definition of security architecture and design is that its a systematic approach to improving network security and mitigating risks. This initial post focuses on the importance of identifying an organizations critical assets and data so it can design a cybersecurity architecture that incorporates controls to protect those systems. Design refers to how the security architecture is built. Security architecture and design looks at how information security controls and safeguards are implemented in IT systems in order to protect the confidentiality integrity and availability of the data that are used processed and stored in those systems.
 Source: pinterest.com
Source: pinterest.com
As part of the Digital practice we are focussed on creating a modern architecture and software development practice that is capable of delivering cloud digital and agile transformations to our clients. The collective features of a cybersecurity architecture include but are not limited to. Cyber security architecture is the design artifacts that describe how the security controls are positioned and how they relate to the overall systems architecture. Endpoint Security Suite Migration and Upgrade. Our service includes consultancy support guidance and advice on the following areas.
 Source: pinterest.com
Source: pinterest.com
Legislative and legal requirements. Let us now begin by understanding cybersecurity architecture. Our Security Architecture Design and Implementation Services give you the expert insight you need to develop and implement security defenses to protect your corporate assets and client data. We at CyberSecure365 assess a number of controls to review the Architecture and Design of any organization in the SABSA framework. While security architecture has many definitions ultimately it is a set of security principles methods and models designed to align to your objectives and help keep your organization safe from cyber threats.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site convienient, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title cyber security architecture design by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






