Your Cloud security architecture design images are available. Cloud security architecture design are a topic that is being searched for and liked by netizens now. You can Get the Cloud security architecture design files here. Download all free photos.
If you’re searching for cloud security architecture design pictures information linked to the cloud security architecture design topic, you have come to the right blog. Our website frequently gives you suggestions for refferencing the maximum quality video and image content, please kindly search and locate more informative video articles and images that fit your interests.
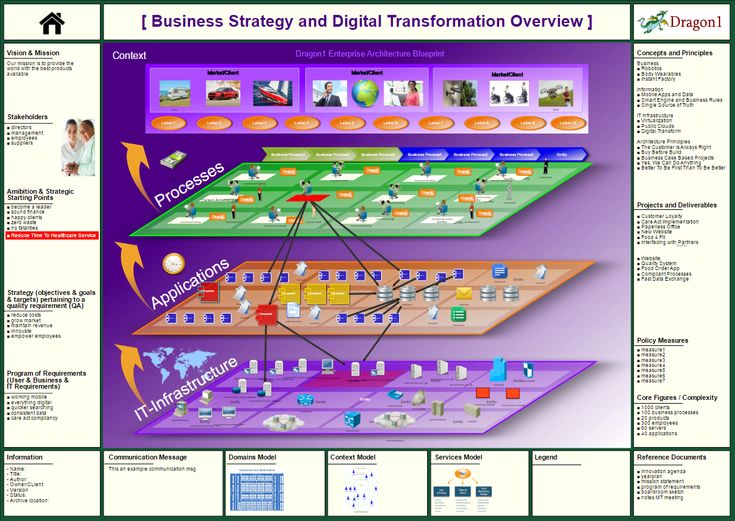
Cloud Security Architecture Design. Projektzusammenarbeit und Datenaustausch in der Cloud. Projektzusammenarbeit und Datenaustausch in der Cloud. What Is Cloud Security Architecture. Secure Systems Research Group- FAU.
 Securing The Internet Of Everything An Architectural View Cisco Blogs Security Architecture Security Internet From pinterest.com
Securing The Internet Of Everything An Architectural View Cisco Blogs Security Architecture Security Internet From pinterest.com
Ad Speichern teilen bearbeiten Sie große Datenmengen zentral für eine optimale Teamarbeit. Inform your security design and test it with penetration testing to simulate. This learning path provides an in-depth look at cloud security architecture. Ad Discover how to overcome the 6 challenges of multicloud security. Step 3 Select the Cloud Ecosystem Architecture93 524 Step 4 Assess Cloud Services94. This Cloud Security Technical Reference Architecture builds on the initiatives above and supports the continued evolution of federal agencies within a rapidly evolving environment and technology landscape through a focus on cloud modernization efforts namely.
Of Computer Science and Engineering Florida Atlantic University Boca Raton FL USA httpwwwcsefauedued edcsefauedu.
Unsere Mission ist es für mehr Gehaltstransparenz in der Arbeitswelt zu sorgen. In addition you want to be able to identify security. Ad Discover how to overcome the 6 challenges of multicloud security. This Cloud Security Technical Reference Architecture builds on the initiatives above and supports the continued evolution of federal agencies within a rapidly evolving environment and technology landscape through a focus on cloud modernization efforts namely. We provide and architectural view of the security issu es to be addressed in cloud computing environment for providing security for the customer. Cloud architectures can help simplify the complex task of securing an enterprise estate through specialization and shared responsibilities.
 Source: pinterest.com
Source: pinterest.com
Cloud Security Architecture and Design Instead of focusing on individual layers of our cloud stack we start day three by building the core security components. Cloud security architecture describes all the hardware and technologies designed to protect data workloads and systems within cloud platforms. Definition There are five best practice areas for security in the cloud. Wie können effektive Simulationen zu mehr Cyber Security führen. We have defined four layers based on.
 Source: pinterest.com
Source: pinterest.com
Before you architect any system you need to put in place practices that influence security. How to secure your multicloud environment with the right security solution. Kostenfreier Report mit praxisnahen Handlungsempfehlungen für mehr Cloud Security. Ad Millionen Gehaltsdaten nützliche Berufsinformationen und tausende Jobangebote. We have defined four layers based on.
 Source: in.pinterest.com
Source: in.pinterest.com
Ad Der TÜViT hat idgard mit dem Trusted Cloud Datenschutzprofil TCDP zertifiziert. The Secure Cloud architecture guide provides. Ad Cloud Security Policy. Ad Speichern teilen bearbeiten Sie große Datenmengen zentral für eine optimale Teamarbeit. This learning path provides an in-depth look at cloud security architecture.
 Source: pinterest.com
Source: pinterest.com
Before you architect any system you need to put in place practices that influence security. SAFE provides the Key to simplify cybersecurity into Secure Places in the Network PINs for. Ad Speichern teilen bearbeiten Sie große Datenmengen zentral für eine optimale Teamarbeit. Cloud security architecture is a security strategy designed around securing an organizations data and applications in the cloud. Projektzusammenarbeit und Datenaustausch in der Cloud.
 Source: pinterest.com
Source: pinterest.com
Cloud security architecture describes all the hardware and technologies designed to protect data workloads and systems within cloud platforms. Unsere Mission ist es für mehr Gehaltstransparenz in der Arbeitswelt zu sorgen. Ad Der TÜViT hat idgard mit dem Trusted Cloud Datenschutzprofil TCDP zertifiziert. Definition There are five best practice areas for security in the cloud. Ad Erfahren Sie warum es wichtig ist die richtigen Motive für die Cloud-Migration zu haben.
 Source: pinterest.com
Source: pinterest.com
Of Computer Science and Engineering Florida Atlantic University Boca Raton FL USA httpwwwcsefauedued edcsefauedu. Shared services designing software in the cloud and cloud security posture management. How to secure your multicloud environment with the right security solution. What Is Cloud Security Architecture. Wie können effektive Simulationen zu mehr Cyber Security führen.
 Source: pinterest.com
Source: pinterest.com
What Is Cloud Security Architecture. Inform your security design and test it with penetration testing to simulate. As you progress through 17 courses youll build your knowledge and skills around cloud infrastructure and design cloud data and application security network security secure storage cryptography secure software development and design data center and physical security and more. Wie können effektive Simulationen zu mehr Cyber Security führen. We have defined four layers based on.
 Source: pinterest.com
Source: pinterest.com
Shared services designing software in the cloud and cloud security posture management. Unsere Mission ist es für mehr Gehaltstransparenz in der Arbeitswelt zu sorgen. Projektzusammenarbeit und Datenaustausch in der Cloud. How to secure your multicloud environment with the right security solution. Of Computer Science and Engineering Florida Atlantic University Boca Raton FL USA httpwwwcsefauedued edcsefauedu.
 Source: pinterest.com
Source: pinterest.com
By architecting to the. We have defined four layers based on. This learning path provides an in-depth look at cloud security architecture. It is a critical extension of enterprise security and it requires an architecture to connect it with an overall security approach. Cloud architectures can help simplify the complex task of securing an enterprise estate through specialization and shared responsibilities.
 Source: pinterest.com
Source: pinterest.com
Think about the architectural capabilities needed across all cloud platforms and in your on-premises environment then consider whether a third-party external control is more suited to your particular requirements. Think about the architectural capabilities needed across all cloud platforms and in your on-premises environment then consider whether a third-party external control is more suited to your particular requirements. Cloud security architecture is a strategy designed to secure and view an enterprises data and collaboration applications in the cloud through the lens of shared responsibility with cloud providers. Before you architect any system you need to put in place practices that influence security. The Secure Cloud architecture guide provides.
 Source: pinterest.com
Source: pinterest.com
Ad Discover how to overcome the 6 challenges of multicloud security. Secure Systems Research Group- FAU. Think about the architectural capabilities needed across all cloud platforms and in your on-premises environment then consider whether a third-party external control is more suited to your particular requirements. Ad Der TÜViT hat idgard mit dem Trusted Cloud Datenschutzprofil TCDP zertifiziert. This learning path provides an in-depth look at cloud security architecture.
 Source: pinterest.com
Source: pinterest.com
It is a critical extension of enterprise security and it requires an architecture to connect it with an overall security approach. This learning path provides an in-depth look at cloud security architecture. Ad Der TÜViT hat idgard mit dem Trusted Cloud Datenschutzprofil TCDP zertifiziert. Identity and Access Management. By architecting to the.
 Source: pinterest.com
Source: pinterest.com
We have defined four layers based on. Unsere Mission ist es für mehr Gehaltstransparenz in der Arbeitswelt zu sorgen. Ad Discover how to overcome the 6 challenges of multicloud security. It is a critical extension of enterprise security and it requires an architecture to connect it with an overall security approach. Ad Speichern teilen bearbeiten Sie große Datenmengen zentral für eine optimale Teamarbeit.
 Source: pinterest.com
Source: pinterest.com
We provide and architectural view of the security issu es to be addressed in cloud computing environment for providing security for the customer. Cloud security architecture is a strategy designed to secure and view an enterprises data and collaboration applications in the cloud through the lens of shared responsibility with cloud providers. This Cloud Security Technical Reference Architecture builds on the initiatives above and supports the continued evolution of federal agencies within a rapidly evolving environment and technology landscape through a focus on cloud modernization efforts namely. Ad Discover how to overcome the 6 challenges of multicloud security. Well break down cloud security architecture best practices and principles that most high-performing teams prioritize when building or.
 Source: pinterest.com
Source: pinterest.com
By architecting to the. We provide and architectural view of the security issu es to be addressed in cloud computing environment for providing security for the customer. Step 3 Select the Cloud Ecosystem Architecture93 524 Step 4 Assess Cloud Services94. Ad Der TÜViT hat idgard mit dem Trusted Cloud Datenschutzprofil TCDP zertifiziert. As more enterprises seek to accelerate their business by shifting data and infrastructure to the cloud security has.
 Source: pinterest.com
Source: pinterest.com
The Zero Trust approach is described in the Security Design Principles section in more detail. Ad Der TÜViT hat idgard mit dem Trusted Cloud Datenschutzprofil TCDP zertifiziert. The Zero Trust approach is described in the Security Design Principles section in more detail. Step 3 Select the Cloud Ecosystem Architecture93 524 Step 4 Assess Cloud Services94. Wie können effektive Simulationen zu mehr Cyber Security führen.
 Source: pinterest.com
Source: pinterest.com
Ad Millionen Gehaltsdaten nützliche Berufsinformationen und tausende Jobangebote. The Zero Trust approach is described in the Security Design Principles section in more detail. Projektzusammenarbeit und Datenaustausch in der Cloud. Your security design and prioritization should be focused on the way attackers see your environment which is often not the way IT and application teams see it. Ad Discover how to overcome the 6 challenges of multicloud security.
 Source: pl.pinterest.com
Source: pl.pinterest.com
Of Computer Science and Engineering Florida Atlantic University Boca Raton FL USA httpwwwcsefauedued edcsefauedu. As more enterprises seek to accelerate their business by shifting data and infrastructure to the cloud security has. The Zero Trust approach is described in the Security Design Principles section in more detail. Ad Erfahren Sie warum es wichtig ist die richtigen Motive für die Cloud-Migration zu haben. Secure Systems Research Group- FAU.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title cloud security architecture design by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.