Your Architecture design and threat modelling images are available. Architecture design and threat modelling are a topic that is being searched for and liked by netizens today. You can Download the Architecture design and threat modelling files here. Find and Download all free photos and vectors.
If you’re looking for architecture design and threat modelling pictures information linked to the architecture design and threat modelling topic, you have come to the ideal blog. Our site always provides you with hints for downloading the maximum quality video and image content, please kindly search and find more informative video content and images that fit your interests.
Architecture Design And Threat Modelling. 17 Central implementation for security controls. Consider all possible threats before the implementation of the smart contract. The following subsections show the details about 41 approach and how this could help in the threat modeling process. To cover topics such as threat modelling secure SDLC or key management users of the MASVS should consult the respective OWASP projects andor.
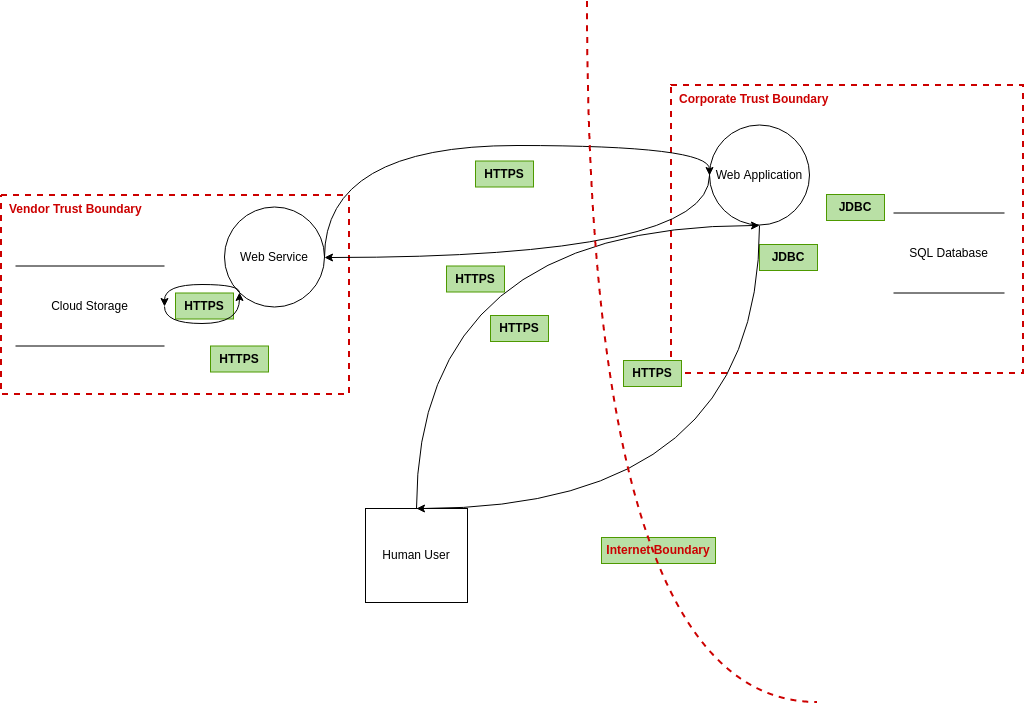 Free Threat Modeling Tool From online.visual-paradigm.com
Free Threat Modeling Tool From online.visual-paradigm.com
Architecture design and threat modelling in the context of creating secure smart contracts. 16 A STRIDE threat model has been produced. 13 A high-level architecture as been defined. It is a wizard-based drag-and-drop tool that you can use to generate threat maps with insights on what to look for. Ensure that a verified contract satisfies the following high-level requirements. Please note that the 41 is comprehensive you may use any other design model during this phase.
Where threat agents exist relative to the architecture Model the location of threat agents motivations skills and capabilities to identify where potential attackers are positioned in relation to your systems architecture.
To cover topics such as threat modelling secure SDLC or key management users of the MASVS should consult the respective OWASP projects andor. Designing for Security Indianapolis IN. Please note that the 41 is comprehensive you may use any other design model during this phase. The category V1 lists requirements pertaining to architecture and design of the app. Consider all possible threats before the implementation of the smart contract. All related smart contracts are identified and used properly.
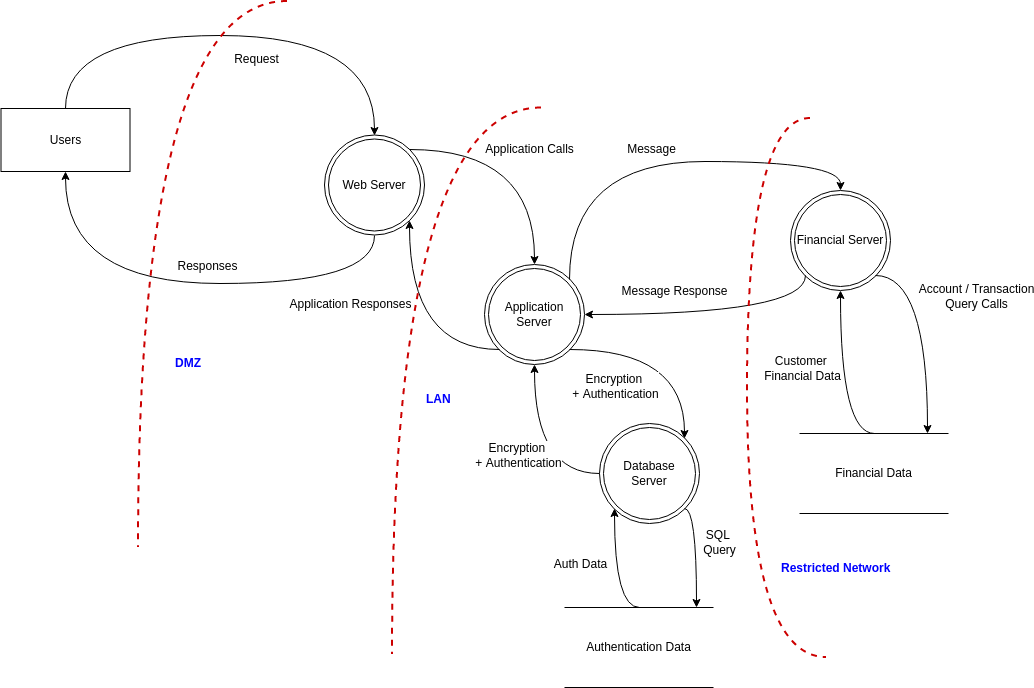 Source: online.visual-paradigm.com
Source: online.visual-paradigm.com
Ensure that a verified contract satisfies the following high-level requirements. 11 All components are identified. Architecture design and threat modelling in the context of creating secure smart contracts. Reference to 41 view model of architecture here. To cover topics such as threat modelling secure SDLC or key management users of the MASVS should consult the respective OWASP projects andor.
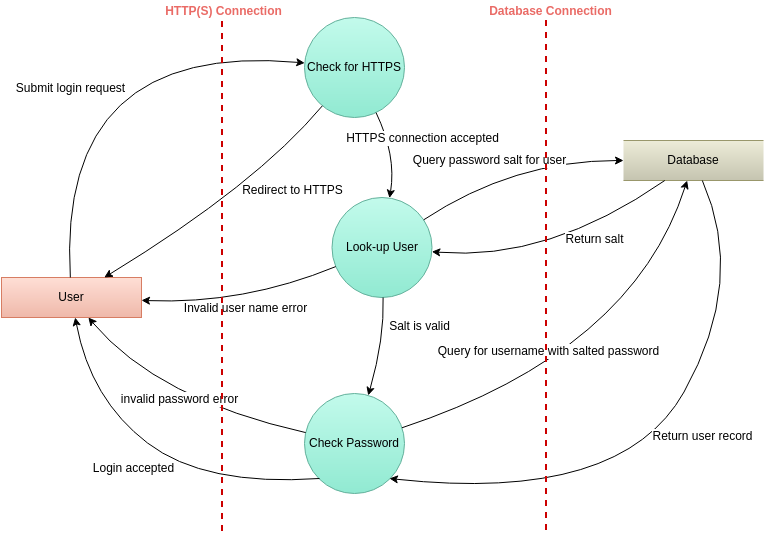 Source: online.visual-paradigm.com
Source: online.visual-paradigm.com
Why is threat modeling needed in the first place. Suggest and manage mitigations for security issues. Ensure that a verified contract satisfies the following high-level requirements. Using threat modeling to think about security requirements can lead to proactive architectural decisions that help reduce threats from the start. All related smart contracts are identified and used properly.
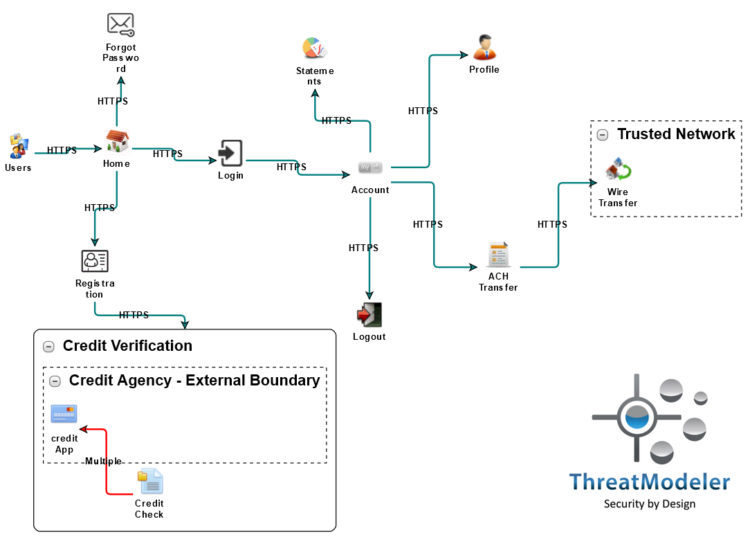 Source: threatmodeler.com
Source: threatmodeler.com
The following subsections show the details about 41 approach and how this could help in the threat modeling process. Security Architecture and Design Threat Modeling Review. Architecture design and threat modelling in the context of creating secure smart contracts. 13 A high-level architecture as been defined. Defendable Architecture as a concept is how to design build operate and defend an infrastructure while continuously applying threat modelling and analysis during each of the process steps in a continuous lifecycle.
 Source: ijcnc.com
Source: ijcnc.com
Risk Develop mitigations and acceptance criteria Can be applied to anythingeven Cloud environments. Security Architecture and Design Threat Modeling Review After going through this course on threat modeling are you better positioned to understand the purpose of threat modeling. To cover topics such as threat modelling secure SDLC or key management users of the MASVS should consult the respective OWASP projects andor. Designing for Security Indianapolis IN. There are various threat modelling methodologies available.
 Source: online.visual-paradigm.com
Source: online.visual-paradigm.com
15 All dependant components are defined. Please note that the 41 is comprehensive you may use any other design model during this phase. Architecture design and threat modelling in the context of creating secure smart contracts. Architecture design and threat modeling in the context of creating secure smart contracts. Designing for Security Indianapolis IN.
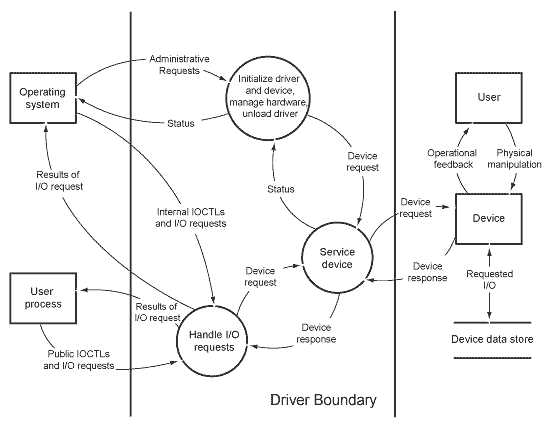 Source: docs.microsoft.com
Source: docs.microsoft.com
The purpose of threat modelling is to provide defenders with a systematic analysis of the probable attackers profile the most likely. Perform a threat model to identify attacks that are unique to how your system is built. 13 A high-level architecture as been defined. With cyber security risk increasing and enterprises becoming more aware of their liabilities software development teams need effective ways to build security into software. Consider all possible threats before the implementation of the smart contract.
 Source: pinterest.com
Source: pinterest.com
Where threat agents exist relative to the architecture Model the location of threat agents motivations skills and capabilities to identify where potential attackers are positioned in relation to your systems architecture. Results in finding architecture bugs earlier. The purpose of threat modelling is to provide defenders with a systematic analysis of the probable attackers profile the most likely. Consider all possible threats before the implementation of the smart contract. Consider all possible threats before the implementation of the smart contract.
 Source: researchgate.net
Source: researchgate.net
Architecture design and threat modeling in the context of creating secure smart contracts. Standing for Visual Agile and Simple Threat modeling it provides actionable outputs for the specific needs of various stakeholders such as application architects and developers cybersecurity personnel etc. Threat modelling is a process by which potential threats can be identified enumerated and prioritised all from a hypothetical attackers point of view. 14 All components are defined. V1 Architecture design and threat modelling.
 Source: synopsys.com
Source: synopsys.com
How does threat modeling help in reducing risk and minimizing attack surfaces. With cyber security risk increasing and enterprises becoming more aware of their liabilities software development teams need effective ways to build security into software. For security audits threat modeling is performed on a completed system or group of systems to provide insight into where to test for weaknesses. There are various threat modelling methodologies available. The following subsections show the details about 41 approach and how this could help in the threat modeling process.

The development team will be able to implement application security as part of the design and development process by using threat modelling to identify threats risks and mitigation during the designing phase. The development team will be able to implement application security as part of the design and development process by using threat modelling to identify threats risks and mitigation during the designing phase. Risk Develop mitigations and acceptance criteria Can be applied to anythingeven Cloud environments. For application design threat modeling is done during design and results in changes to a systems design. Architecture design and threat modeling in the context of creating secure smart contracts.
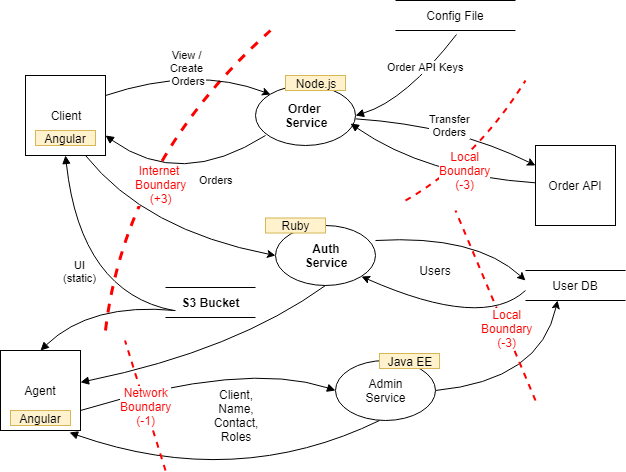 Source: secodis.com
Source: secodis.com
16 A STRIDE threat model has been produced. Please review papers and provide the summary 2-3 pages. Consider all possible threats before the implementation of the smart contract. VAST offers a unique application and infrastructure visualization plan so that the creation and use of threat models dont require any. Architecture design and threat modeling in the context of creating secure smart contracts.
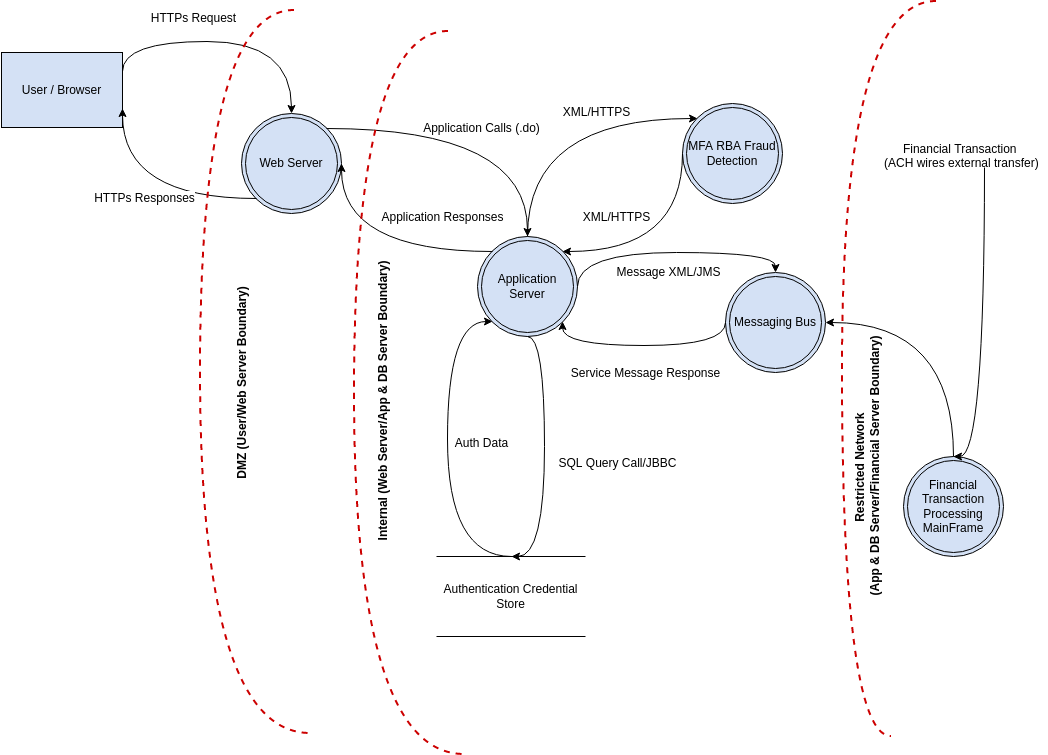 Source: online.visual-paradigm.com
Source: online.visual-paradigm.com
Threat modelling is a risk-based approach to designing secure systems. Defendable Architecture as a concept is how to design build operate and defend an infrastructure while continuously applying threat modelling and analysis during each of the process steps in a continuous lifecycle. For security audits threat modeling is performed on a completed system or group of systems to provide insight into where to test for weaknesses. Threat modelling is a process by which potential threats can be identified enumerated and prioritised all from a hypothetical attackers point of view. Iriusrisk is a threat modeling tool that performs risk analysis and generates a threat model of a software application at the design phase with recommendations on how to address the risk.
 Source: insights.sei.cmu.edu
Source: insights.sei.cmu.edu
All related smart contracts are identified and used properly. Modeling Risks Programmatically Training Requirements Design Implementation Verification Release Response Microsoft SDL Process Developing Threat Models Structured approach Repeatable way to identify attack surfaces ie. For security audits threat modeling is performed on a completed system or group of systems to provide insight into where to test for weaknesses. Where threat agents exist relative to the architecture Model the location of threat agents motivations skills and capabilities to identify where potential attackers are positioned in relation to your systems architecture. The category V1 lists requirements pertaining to architecture and design of the app.
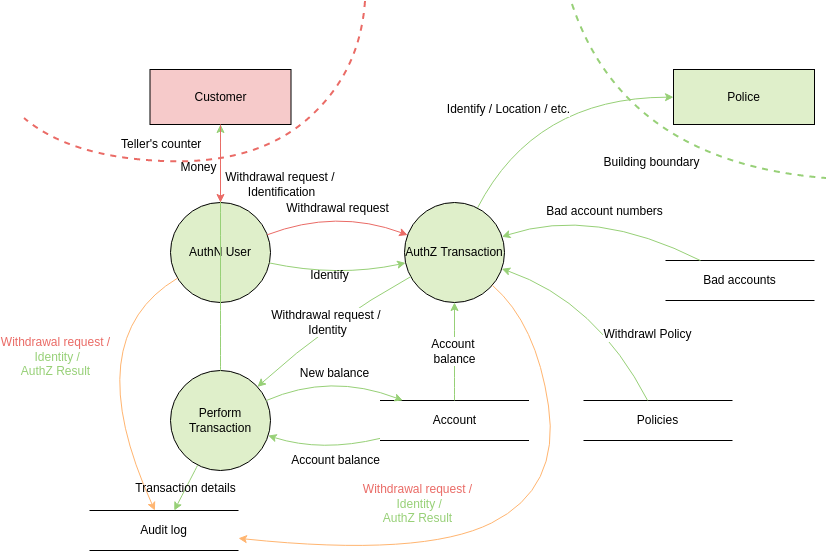 Source: online.visual-paradigm.com
Source: online.visual-paradigm.com
As such this is the only category that does not map to technical test cases in the OWASP Mobile Testing Guide. Threat modelling is a risk-based approach to designing secure systems. VAST offers a unique application and infrastructure visualization plan so that the creation and use of threat models dont require any. Security Architecture and Design Threat Modeling Review. All related smart contracts are identified and used properly.
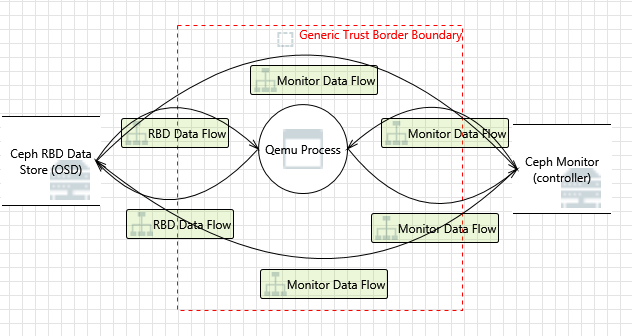 Source: docs.mirantis.com
Source: docs.mirantis.com
How does threat modeling help in reducing risk and minimizing attack surfaces. Ensure that a verified contract satisfies the following high-level requirements. In this context threat modeling is a Solution Architecture or Security Architecture activity. Iriusrisk is a threat modeling tool with architectural design and questionnaires defined by an expert system that explains the technical architecture the features and the security context of the application. Threat modelling is a process by which potential threats can be identified enumerated and prioritised all from a hypothetical attackers point of view.
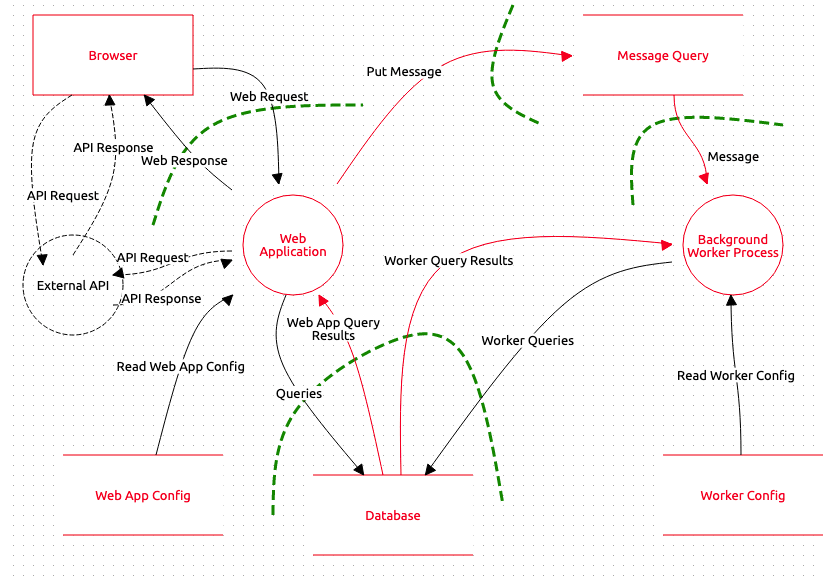 Source: dev.to
Source: dev.to
16 A STRIDE threat model has been produced. What is Threat Modelling. In this context threat modeling is a Solution Architecture or Security Architecture activity. To cover topics such as threat modelling secure SDLC or key management users of the MASVS should consult the respective OWASP projects andor. Ensure that a verified contract satisfies the following high-level requirements.
 Source: resources.infosecinstitute.com
Source: resources.infosecinstitute.com
Modeling Risks Programmatically Training Requirements Design Implementation Verification Release Response Microsoft SDL Process Developing Threat Models Structured approach Repeatable way to identify attack surfaces ie. In order to enable a targeted and focused approach for implementing security one must identify what assets to defend and what. 17 Central implementation for security controls. Architecture design and threat modeling in the context of creating secure smart contracts. To cover topics such as threat modelling secure SDLC or key management users of the MASVS should consult the respective OWASP projects andor.
 Source: toolbox.com
Source: toolbox.com
Ensure that a verified contract satisfies the following high-level requirements. VAST offers a unique application and infrastructure visualization plan so that the creation and use of threat models dont require any. Logical View Create a logical map of the Target of Evaluation. 14 All components are defined. V1 Architecture design and threat modelling.
This site is an open community for users to submit their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site helpful, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title architecture design and threat modelling by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






